An exposed financial network doesn’t have hours; it has minutes. It takes less than 60 minutes. That’s all a hacker needs to infiltrate an exposed financial network. Once they’re in, the damage can unfold in minutes, often faster than IT teams can detect the exposure.
The stakes for financial institutions couldn’t be higher. These systems handle some of the most valuable data on the Internet—account numbers, credit card information, transaction histories, and personally identifiable information (PII).
Attackers are now armed with AI-powered malware, hyper-targeted phishing schemes, and advanced social engineering tactics that bypass well-established security protocols. These sophisticated tactics, including social engineering and AI-powered malware, make standard security measures ineffective.
Meanwhile, institutions face pressure from strict regulatory frameworks like GDPR, CCPA, SOX, GLBA, and PCI DSS. These regulations mandate encryption, access controls, breach reporting, and regular audits.
To stay ahead, financial organizations are turning to a new line of defense: AI-powered cybersecurity.
In this blog, we’ll explore how artificial intelligence is reshaping threat detection, fraud prevention, and regulatory compliance and how it may be the most potent measure to secure financial data.
Current Challenges in Compliance and Data Security
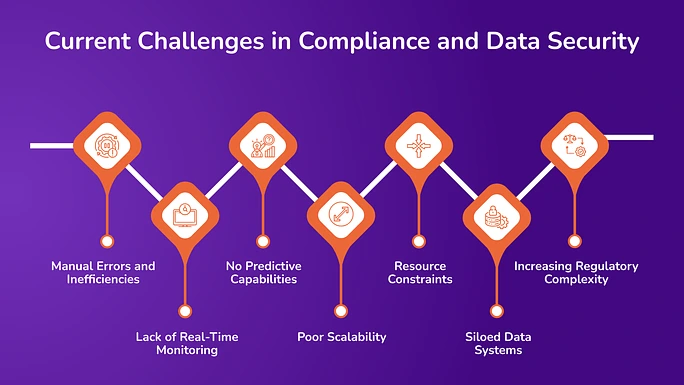
Conventional data protection and compliance methods struggle to meet the demands of the present financial environment. Here are a few challenges that organizations face:
1. Manual Errors and Inefficiencies
Most compliance processes still depend on manual tasks like data tagging, audit preparation, and report generation. These are time-consuming and prone to human error. Mistakes in classification, reporting delays, or documentation inconsistencies can lead to compliance violations and financial penalties.
2. Lack of Real-Time Monitoring
Legacy systems often can’t monitor data activity in real time. This delay prevents organizations from spotting unauthorized access or unusual behavior quickly. As a result, threats may go undetected for too long, increasing the impact of potential breaches.
3. No Predictive Capabilities
Conventional tools react to problems after they happen. They don’t help anticipate risks based on patterns or past data. This reactive method limits an organization’s ability to prevent incidents before they escalate into compliance issues or data loss.
4. Poor Scalability
As organizations grow, so does their data. Regular compliance systems are not made to handle large, complex datasets or multiple systems across regions. Manual oversight becomes less reliable, making processes more challenging to manage at scale.
5. Resource Constraints
Compliance teams often have limited staff and budgets. Manual work takes up time that could be used for higher-value tasks. This leads to slow responses to regulatory changes and delays in addressing security gaps.
6. Siloed Data Systems
In many organizations, data is stored across disconnected systems. This fragmentation makes it challenging to get a comprehensive view of compliance status or identify risks that span departments or platforms.
7. Increasing Regulatory Complexity
The volume and variety of global financial regulations are growing. Manually tracking evolving requirements is difficult and increases the risk of missing important updates or applying outdated policies.
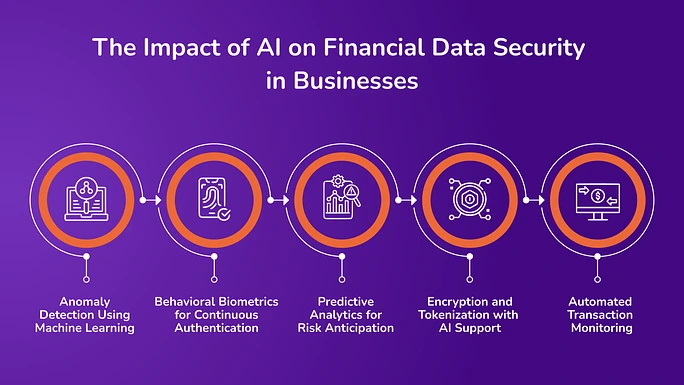
The Impact of AI on Financial Data Security in Businesses
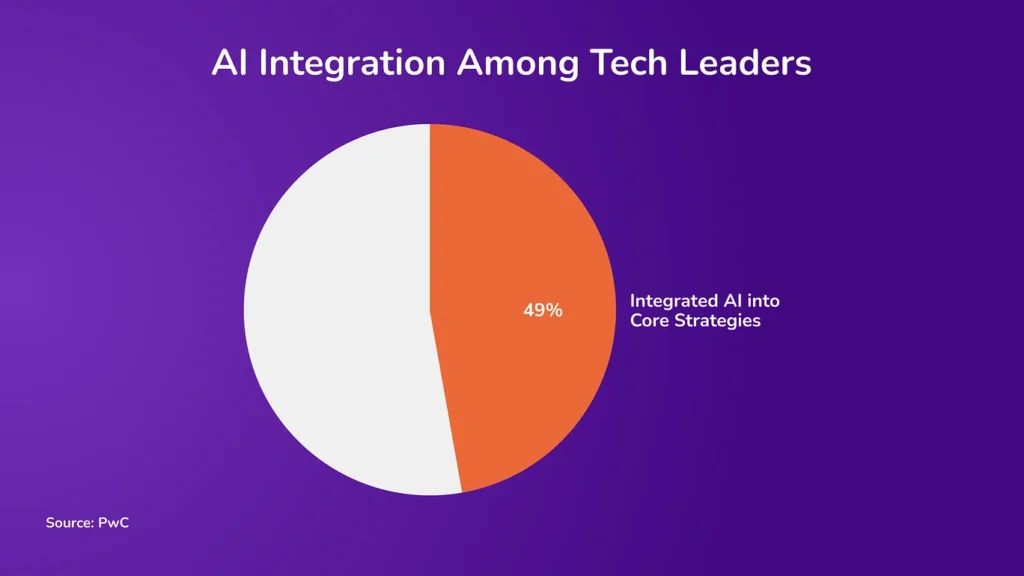
According to PwC’s 2025 AI Business Predictions Report, 49% of technology leaders reported that AI was fully integrated into their companies’ core business strategies. Here are some of the essential artificial intelligence applications that play a vital role in protecting financial data:
1. Anomaly Detection Using Machine Learning
AI-based anomaly detection systems analyze massive volumes of transactional and behavioral data in real time to identify deviations from expected patterns. These systems are trained on historical data to learn what “normal” looks like for each user or system, enabling them to detect unusual behavior such as rapid spending spikes, foreign transactions, or access from unfamiliar devices. Here is how these systems protect data:
- Model Training: Historical transaction data is used to establish normal behavioral baselines.
- Real-Time Monitoring: The AI system compares incoming data against the baseline.
- Alert Generation: The system triggers alerts or temporarily halts the activity if a transaction or access pattern deviates significantly (e.g., spending far above normal limits or login attempts from different locations).
Here are a few AI models utilized for this application:
| AI Models | Description |
| Supervised Machine Learning | Trains algorithms on a labeled dataset, teaching them to make predictions or decisions based on past examples. |
| Unsupervised Machine Learning | Analyze and cluster unlabeled data based on similarities and patterns without prior training. |
| Semi-Supervised Machine Learning | Combines a small amount of labeled data with a large amount of unlabeled data to improve learning accuracy. |
| Statistical Modeling | Uses statistics to estimate relationships among variables to predict outcomes based on historical data. |
| Clustering Algorithms | Group a set of objects so that objects in the same group are more similar than those in other groups. |
| Time-Series Analysis | Analyze data points arranged chronologically to identify trends, cycles, or seasonal variations. |
For example, JPMorgan Chase & Co. uses AI to monitor real-time transactions, detecting anomalies like unusually large purchases or sudden location changes. This effectively prevents potential fraud and enhances customer security.
2. Behavioral Biometrics for Continuous Authentication
Behavioral biometrics use AI to continuously authenticate users based on how they interact with systems, such as how they type, move a mouse, swipe a screen, or speak. These patterns are unique to individuals and difficult to replicate, providing an additional layer of security beyond passwords and tokens. Here is how it can be implemented for data protection:
- Data Collection: The system captures user inputs like typing speed, touchscreen pressure, and navigation flow.
- Pattern Learning: Machine learning models identify a user’s typical behavioral signature.
- Anomaly Detection: The system flags the session if someone logs in with the correct credentials but behaves differently (e.g., has an unusual typing rhythm).
- Intervention: Triggers additional verification or session termination if high risk is detected.
The following technologies are employed within this application:
| AI Models | Application |
| AI-Driven Behavioral Analytics | Uses artificial intelligence to analyze user behavior patterns to detect anomalies and predict future actions. |
| Biometric Data Processing | Involves analyzing physical or behavioral human characteristics, such as fingerprints or voice patterns, for authentication and identification purposes. |
| Continuous Authentication Algorithms | Constantly verifies the identity of a user based on their activities and behaviors while logged into a system. |
| Real-Time Risk Scoring | Calculates the risk level of a transaction or user activity instantly, using dynamic data to identify potential threats as they occur. |
3. Predictive Analytics for Risk Anticipation
Predictive analytics allows institutions to foresee risks by analyzing past data and spotting trends that could lead to future incidents. These insights help mitigate vulnerabilities and strengthen data protection strategies before breaches occur. Here is how it works:
- Historical Analysis: AI models process historical financial and behavioral data to recognize leading fraud or system failure indicators.
- Scenario Simulation: Systems simulate attack vectors or fraud scenarios to assess potential weaknesses.
- Proactive Mitigation: Before escalating, the institution can address emerging risks, such as outdated access policies or transactional anomalies.
Technologies used in this application include:
| AI Models | Description |
| Predictive Modeling | Utilizes historical data and statistics to forecast future events, helping to make informed decisions based on likely outcomes. |
| Regression Analysis | A statistical method that examines the relationship between a dependent variable and one or more independent variables to find trends or predict future values. |
| Neural Networks | Mimics the human brain’s structure and function, learning and making decisions by processing complex data patterns through interconnected layers of nodes. |
| Time-Series Forecasting | Analyzes data points collected or recorded at specific intervals to predict future values based on historical trends and time-dependent patterns. |
| Decision Trees | A graphical model that uses a branching method to illustrate every possible outcome of a decision, helping to analyze the consequences of different choices. |
For example, American Express uses predictive analytics to analyze historical transaction data and simulate fraud scenarios, enabling proactive identification and mitigation of potential security threats. This approach enhances fraud prevention mechanisms and customer trust by addressing risks before they materialize.
4. Encryption and Tokenization with AI Support
Encryption and tokenization protect sensitive financial data by making it unreadable or replacing it with non-sensitive equivalents. AI enhances these methods by automating key management, optimizing encryption strength, and identifying security gaps. Here is how this process works:
- Encryption: AI dynamically manages encryption keys and adapts cryptographic strength based on threat levels.
- Tokenization: Sensitive data (e.g., credit card numbers) is replaced with tokens, and AI tracks token mapping without storing original values in live systems.
- Threat Detection: AI identifies anomalies, such as irregular data access attempts, and triggers key rotation or encryption updates.
Here are the technologies utilized for this application:
| AI Models | Description |
| AI-Augmented Key Management Systems | Streamlines cryptographic key management with AI. |
| Symmetric and Asymmetric Encryption Algorithms | Secures data using two encryption styles for enhanced safety. |
| Tokenization Engines | Safeguards sensitive data by converting it into secure tokens. |
| AI-Based Vulnerability Scanning | Uses AI to detect and address security vulnerabilities efficiently. |
5. Automated Transaction Monitoring
AI automates the monitoring of financial transactions to ensure they follow internal policies and regulatory standards. It identifies suspicious activity and supports compliance teams by reducing manual review workloads. Here is how it works:
- Live Analysis: Transactions are reviewed in real time, detecting abnormal frequency, amount, or geography.
- Pattern Matching: Models compare current behavior to typical activity across similar profiles.
- Adaptive Learning: Systems adjust thresholds as they learn new fraud tactics or regulatory changes.
Technologies used in this application include:
| AI Models | Description |
| Real-Time AI Monitoring Systems | Monitors data continuously to provide instant insights and responses. |
| Pattern Recognition Models | Identifies patterns and trends in data to enhance decision-making. |
| Decision Support Systems | Provides analytical tools and data to support complex decision processes. |
| NLP for Transaction Context Analysis | Uses natural language processing to understand and analyze the context of transactions. |
For example, PayPal employs automated transaction monitoring to analyze real-time transactions for anomalies in frequency, amount, or geography. It adaptively learns to detect new fraud patterns and comply with regulatory changes, enhancing security and efficiency.
AI’s Role in Compliance: How It Helps Organizations Meet Regulatory Demands
As regulatory environments grow more complex, financial institutions are under increasing pressure to meet compliance standards without sacrificing operational efficiency. Here are some of the AI-driven applications that support financial regulatory compliance:
1. AI-powered Compliance Monitoring Tools
AI-driven compliance monitoring systems continuously scan transactions, communications, and internal processes to ensure alignment with current regulatory requirements. These tools adapt to new legal changes and automatically adjust monitoring parameters without manual updates.
The system reviews incoming and outgoing data to identify potential compliance breaches. It uses AI to analyze legal texts and update business rules based on changes in applicable laws. Non-compliant activities trigger immediate alerts for review by compliance teams.
2. Intelligent KYC and CIP Verification
By automating identity verification, AI accelerates Know Your Customer (KYC) and Customer Identification Program (CIP) procedures. It helps financial institutions validate customer documents, cross-check data across databases, and flag inconsistencies.
AI uses OCR and computer vision to extract information from scanned IDs, utility bills, and other documents. Systems match the extracted data with government or third-party databases. AI spots forged or altered documents and detects signs of impersonation.
3. Anti-Money Laundering (AML) Risk Monitoring
AI strengthens AML efforts by identifying suspicious transaction patterns and scoring clients’ or accounts’ risk levels dynamically. It enables continuous monitoring and supports compliance with AML reporting requirements.
AI monitors real-time flows for red flags, such as frequent transfers just below reporting thresholds, and assigns dynamic risk scores based on transaction behavior, geography, and industry. AI helps generate Suspicious Activity Reports (SARs) with relevant supporting data.
4. Intelligent Document Processing (IDP) for Regulatory Review
IDP automates reviewing and processing regulatory documents such as compliance reports, audit logs, and regulatory filings. It improves the accuracy and speed of documentation required during audits or regulatory reviews.
AI pulls relevant data points from large volumes of structured and unstructured documents.
NLP classifies content like privacy policies, audit trails, or consent logs. Documents are checked against predefined rules for completeness and accuracy.
5. AI for Regulatory Text Analysis and Change Management
AI helps interpret and track updates in legal and regulatory documents. It extracts obligations from regulatory texts and maps them to internal policies and procedures to ensure compliance.
NLP parses complex legal language to identify requirements. It helps extract obligations that are linked to business policies or controls. AI monitors legal updates and highlights what has changed from previous versions.
Why Choose Avahi for Your AI Implementation and Development?
Avahi provides a streamlined platform for businesses to build and deploy powerful GenAI applications without needing dedicated machine learning engineers or data scientists. Avahi AI Platform is tailored to accelerate development, reduce operational complexity, and enhance outcomes in key areas like financial data protection and regulatory compliance. Here’s why Avahi is a smart choice:
1. Simple Integration into Existing Systems

Avahi’s GenAI platform is built for compatibility. It allows you to integrate AI-powered features directly into your existing data infrastructure and applications without complex migrations, ensuring a smooth transition and minimal disruption to business operations.
2. Unmatched Speed in Deployment
Deploy AI applications within minutes using Avahi’s prebuilt components and templates. This is ideal for financial institutions that need to implement fraud detection, automated compliance checks, or internal risk monitoring tools quickly.
3. Faster Time-to-Market
Shorten development cycles with prepackaged GenAI solutions. Avahi enables you to bring ideas to production faster, whether building a compliance dashboard or an AI-assisted document analysis tool.
4. Automation for Internal Workflows
Automating internal tasks such as KYC verification, regulatory reporting, and audit documentation can reduce manual workloads and support compliance teams in more efficiently managing complex regulatory demands.
5. Rapid Custom Application Development
Build and customize GenAI applications using pre-configured prompts. Financial teams can create tools for fraud analysis, client onboarding, or automated risk profiling with minimal technical setup.
6. Structured Extraction
Extract data from scanned documents, ID cards, or bank statements using built-in Optical Character Recognition (OCR). This supports faster and more accurate identity verification and document processing during KYC and AML procedures.
7. Personalized Marketing Campaigns
Create AI-driven, compliant marketing messages that align with customer data privacy standards. Avahi enables targeted outreach while respecting regulatory requirements like GDPR and CCPA.
8. Data-Driven Insights
Transform natural language questions into SQL queries and extract actionable insights from structured financial datasets. This enables decision-makers to access real-time compliance and risk data without writing complex code.
Discover Avahi’s AI Platform in Action
At Avahi, we empower businesses to deploy advanced Generative AI that streamlines operations, enhances decision-making, and accelerates innovation—all with zero complexity.
As your trusted AWS Cloud Consulting Partner, we empower organizations to harness AI’s full potential while ensuring security, scalability, and compliance with industry-leading cloud solutions.
Our AI Solutions include:
- AI Adoption & Integration – Utilize Amazon Bedrock and GenAI to enhance automation and decision-making.
- Custom AI Development – Build intelligent applications tailored to your business needs.
- AI Model Optimization – Seamlessly switch between AI models with automated cost, accuracy, and performance comparisons.
- AI Automation – Automate repetitive tasks and free up time for strategic growth.
- Advanced Security & AI Governance – Ensure compliance, fraud detection, and secure model deployment.
Want to unlock the power of AI with enterprise-grade security and efficiency? Get started with Avahi’s Gen AI Platform!